Translated
from http://hlbr.sourceforge.net/ips.html
by
André Bertelli Araújo
(lliberte a gmail
com).
Last update:
18 Dec 05.
IPS
DefinitionIPS (Intrusion Prevention
System) is a
system similar to an IDS (Intrusion Detection System), but with the
goal of actively preventing an attack, not only detecting it. The
difference between the two is that an IPS, in addition of being able to
detect anomalous traffic, is also able to handle it. This way, it's
possible to achieve a higer degree of network security. IPS are
components in a firewall system.
Many don't know the correct meaning of the word firewall. Firewall is an integrated protection system used in computer networks. This system is made of packet filters, state filters, IDS, IPS, proxies, network antivirus, etc. So, for example, it is wrong that a machine running Iptables is the firewall of a network. That's because Iptables is merely a packet and states filter. It can only analyse data from the headers of the IP packets passing through it (this means only source and destination addresses, source and destination ports, transport protocol used, and so on). A packet and states filter can't, for example, analyse the contents of a packet (payload). Assuming that any machine in the internet can connect to the port 80 of our web server or to the port 25 of our e-mail server, a packet with an attack or virus will pass through Iptables and will get in our network. Iptables only checks the packet source and destination, ignoring its contents.
The following picture shows an example of a firewall system. The gray area represents the system.
In this case the IPS used, HLBR, was positioned before the iptables packet filter. This way we can even protect the iptables machine itself. It is also clear from the picture that it isn't possible to provide a reasonable degree of security to a network only with a machine running a packet and states filter (as people usually do).
Now, look at the following picture:
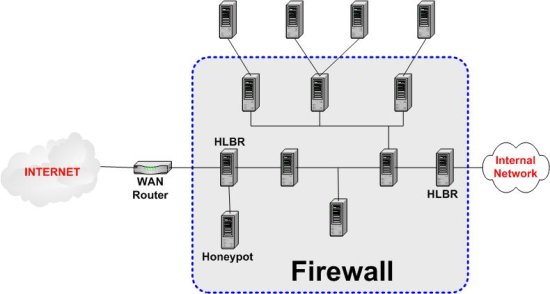
Another HLBR was connected between the internal network and the network servers, in order to provide an even higher degree of security to these servers. Also, a honeypot or honeynet was implemented just after the Internet, because HLBR can divert the attacks to that honeypot/net.
The most important conclusion is that a firewall system must be made from several security elements. Each element works in a different way and one doesn't replace the others.
Firewall
systems
Many don't know the correct meaning of the word firewall. Firewall is an integrated protection system used in computer networks. This system is made of packet filters, state filters, IDS, IPS, proxies, network antivirus, etc. So, for example, it is wrong that a machine running Iptables is the firewall of a network. That's because Iptables is merely a packet and states filter. It can only analyse data from the headers of the IP packets passing through it (this means only source and destination addresses, source and destination ports, transport protocol used, and so on). A packet and states filter can't, for example, analyse the contents of a packet (payload). Assuming that any machine in the internet can connect to the port 80 of our web server or to the port 25 of our e-mail server, a packet with an attack or virus will pass through Iptables and will get in our network. Iptables only checks the packet source and destination, ignoring its contents.
The following picture shows an example of a firewall system. The gray area represents the system.

In this case the IPS used, HLBR, was positioned before the iptables packet filter. This way we can even protect the iptables machine itself. It is also clear from the picture that it isn't possible to provide a reasonable degree of security to a network only with a machine running a packet and states filter (as people usually do).
Now, look at the following picture:

Another HLBR was connected between the internal network and the network servers, in order to provide an even higher degree of security to these servers. Also, a honeypot or honeynet was implemented just after the Internet, because HLBR can divert the attacks to that honeypot/net.
The most important conclusion is that a firewall system must be made from several security elements. Each element works in a different way and one doesn't replace the others.
